
19Aug
In the modern enterprise, identity has become the new perimeter. Adversaries no longer need to break down firewalls—they simply log in. Identity-driven attacks exploit stolen or compromised credentials to impersonate legitimate users, giving attackers unrestricted access to sensitive systems and data while bypassing traditional security controls.
Once in possession of valid credentials, threat actors can:
• Authenticate as a legitimate user without raising traditional intrusion alarms.
• Bypass multi-factor authentication using session hijacking, token theft, or MFA fatigue attacks.
• Move laterally across cloud and on-prem systems via Single Sign-On (SSO) or federated identity services.
• Escalate privileges by abusing admin accounts, service accounts, or misconfigured role assignments.
These techniques allow attackers to operate under the radar for weeks or months, making identity-driven attacks both stealthy and high-impact.
How Labyrinth Disrupts Identity-Based Threats
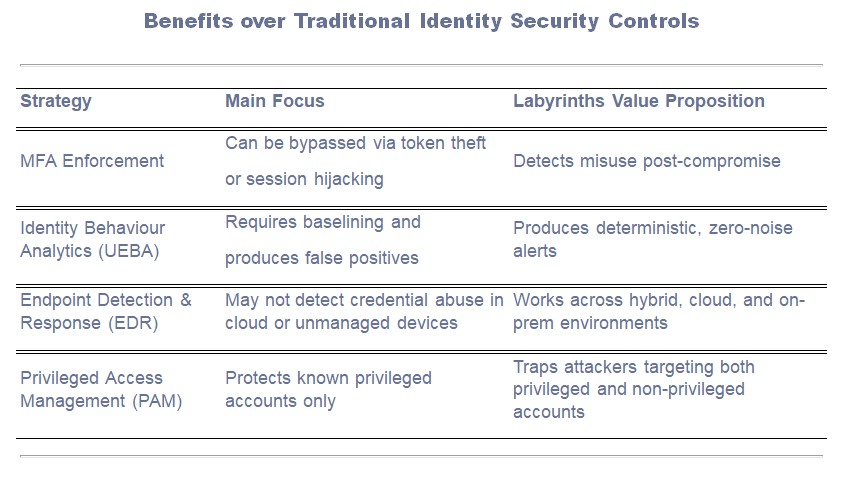
Labyrinth Deception Platform introduces a proactive defence layer that turns the attacker’s reliance on identity into a liability. Unlike purely detective measures such as SIEM rules or behavioural analytics, Labyrinth creates an active deception fabric across the environment.
The Platform injects believable hosts, shares, and applications into the network’s visible attack surface. These decoy systems are instrumented to log every action, providing forensic-grade telemetry on attacker behaviour without putting production systems at risk.
Labyrinth monitors for attempts to access privileged roles, sensitive APIs, or critical file shares that are actually part of the deception layer. Any interaction generates high-confidence alerts—no baselining or anomaly detection required.
Because these deceptive assets appear as attractive, high-value targets, attackers are drawn to them early in their campaign—often during credential validation or initial reconnaissance—long before they can exfiltrate data or damage infrastructure.
When a threat actor—whether an external infiltrator or an insider—attempts to use stolen credentials, they are drawn toward deceptive assets. The moment they interact, Labyrinth triggers high-fidelity alerts, enabling security teams to respond before real damage occurs. This proactive approach not only detects identity misuse early but also disrupts the attacker’s playbook, making lateral movement and privilege escalation dangerous for them.
Conclusion
In an era where over 80% of breaches involve stolen or misused credentials, identity-driven attacks are the most insidious threat to enterprises. The Labyrinth Deception Platform turns the attacker’s reliance on identity into their undoing—embedding deception into every layer of the environment, detecting misuse instantly, and empowering security teams to stop breaches before they escalate.
With Labyrinth, the question isn’t if you’ll detect an identity-based attack—it’s how early you’ll catch it.

